Veil: Privacy without Bounds Complete Review

While many cryptocurrencies make claims without doing anything differently, the Veil platform appears to use a distinct actionable plan to salvage the privacy situation in the cryptocurrency world.
While most of the cryptocurrency platforms depend on older versions of the blockchain software, the Veil platform uses one of the most advanced forms – Bitcoin version 0.17.1. This ensures the security of the assets of users that use the platform. While this bitcoin version isn’t exactly new, it’s has been confirmed to be the most resilient of the many versions in existence.
One of the strengths of the Veil platform is its use of the Zerocoin protocol. This protocol uses cryptography to ensure the confirmation of transactions without offering any exact route regarding the arrival at such a destination. Apparently, the process of a transaction is shrouded in mystery thanks to this protocol.
Underlying Technology
Zerocoin Protocol and RingCT technology
First, what is Zerocoin?
A technology that aims to ensure privacy for users in the bitcoin network. It is the initial version of ZeroCash protocol, the technology that is now used by ZCash.

Overview for it’s Underlying Technology :
Bulletproof. Privacy wise, I could say Veil is in the same level as Monero and ZCash but with no exposure.
Hybrid Consensus PoS/PoW
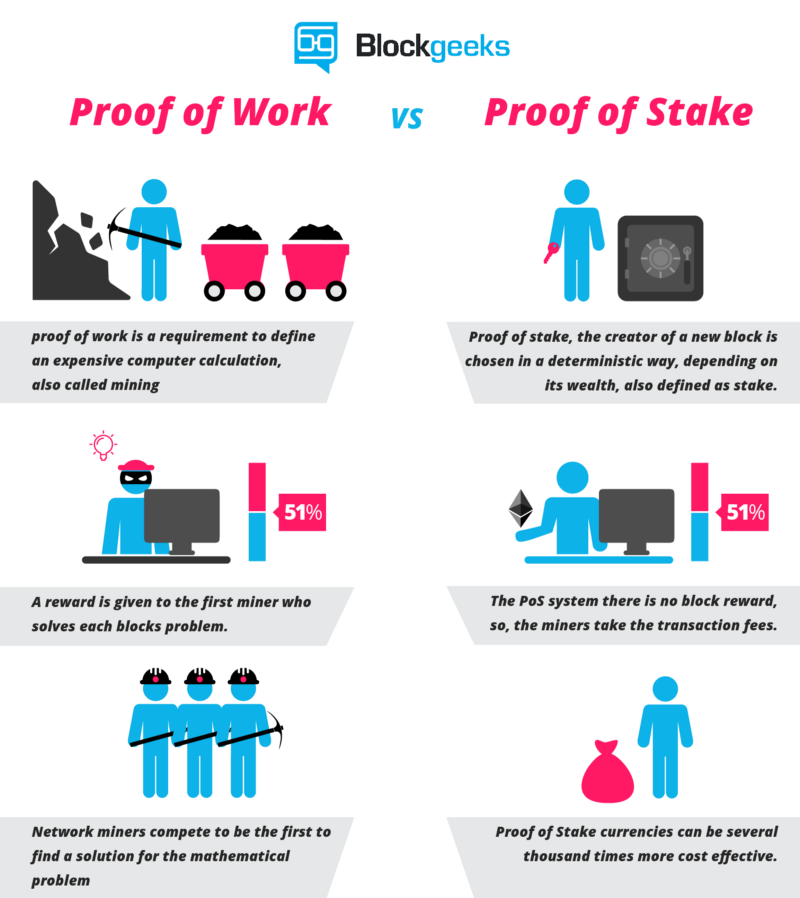
Proof of Stake (PoS)
The concept states that a person can mine or validate block transactions according to how many coins he or she holds.
In this way, all Veil holders would benefit in earning rewards thru the staking process in the form of Zerocoin Veil.
PoS Difficulty : 9000670.043959823 (at the time of writing)
Proof of Work (PoW)
Is the original consensus algorithm in a Blockchain network where miners compete against each other to complete transactions on the network and get rewarded.
With the X16RT hashing algorithm, only NVIDIA and AMD processors are allowed to mine Veil and provide security against 51% attacks.
PoW Difficulty : 5373.591054736813 (at the time of writing)
One of the strengths of the Veil platform is its use of the Zerocoin protocol. This protocol uses cryptography to ensure the confirmation of transactions without offering any exact route regarding the arrival at such a destination. Apparently, the process of a transaction is shrouded in mystery thanks to this protocol.
The use of the Dandelion protocol improves on the privacy protection of the Veil platform. Using the recently updated Dandelion++ protocol, transactions on the blockchain are shielded from identification using a privacy graph. The source node responsible for the sending of the cryptocurrency is never revealed.
Though the Veil platform will have mining activities enabled, this will be done in a well-ordered manner. Its proof-of-work system ensures coins are disbursed properly and securely without any problems. The use of the ASIC-resistant X16RT hashing algorithm adds another layer of security which users are provided with on the platform.
Veil mining software and pools
Mainnet — https://explorer.veil-project.com/
Testnet — https://testnet.veil-project.com/
Mining Software
Suprminer (NVIDIA)
CryptoDredge (NVIDIA)
T-Rex (NVIDIA)
Wildrig (AMD)
Mining Pools
Veilmine
Suprnova
BSOD
Coinblockers
NLpool
NoSuchPool
Blockmasters
1stMiningPool
Source : https://veil-project.com/mining/

For more insight about this incredible platform(veil) do click on the link below
Website: https://veil-project.com/
Reddit: https://www.reddit.com/r/veil
ANN Thread: https://bitcointalk.org/index.php?topic=5065331.0
Telegram: https://t.me/VEILProject
Discord: https://discord.veil-project.com/
Linkedln: https://www.linkedin.com/company/project-veil/
Author:
Bitcointalk username: gaitonde
Bitcointalk profile link: https://bitcointalk.org/index.php?action=profile;u=2344636
Eth Address: 0x3685ff77f8e4deEc9abe29ceA15E33209863d4CD